How to use port call waiting to secure an SSH service on Linux
Port call waiting is a great technique for controlling access to a port by allowing only legitimate users to access the service running on the server. It works in such a way that when the correct connection attempt sequence is established, the firewall will preferably open a closed port.
The logic of port knocking is to protect your Linux system from automatic port scanners barking at open ports. In this guide, we will look at how to set up port call waiting and how to configure it to secure your SSH service. For demonstration purposes we use Ubuntu 18.04.
Step 1: Install and configure knockd
To get started, log in to your Linux system and install knockd daemon as shown.
$ sudo apt install knockd
Once installed, open knockd.conf configuration with the desired text editor. Here we use the vim command line text editor.
$ sudo vim /etc/knockd.conf
The default configuration file is displayed as follows.
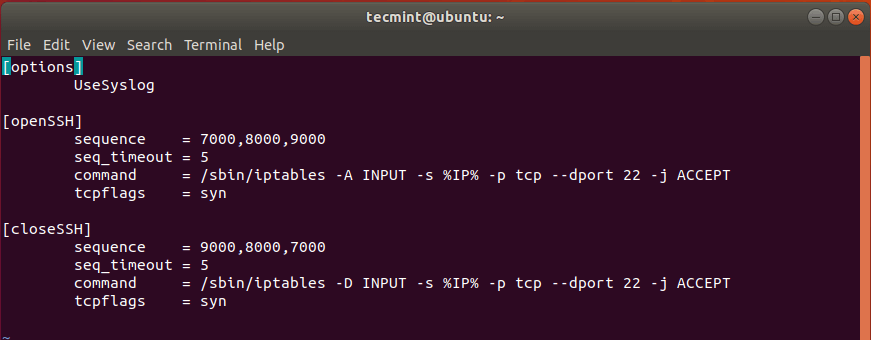
Below [openSSH] section, we need to change the default call waiting order – 7000,8000,9000 – to something else. This is because these values are already known and can compromise system security.
For testing purposes, we have set the values to 10005, 10006, 10007. This sequence is used to open the SSH port from the client system.
On the third line – from command, change -A that -I Right after it /sbin/iptables command and before INPUT.
And lastly, [closeSSH] section, change the default sequence to the desired selection. This sequence is used to close the SSH connection when the user is ready and logs out of the server.
Here is our complete lineup.
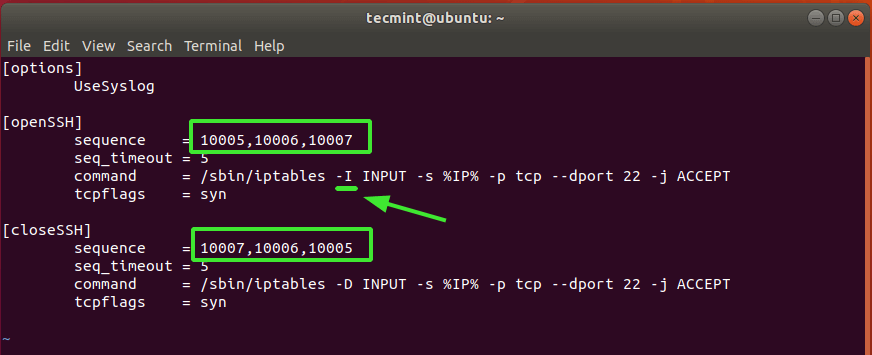
When you’re done, save your changes and exit.
Another lineup that we need to change is / etc / default / knockd. Open again with a text editor.
$ sudo vim /etc/default/knockd
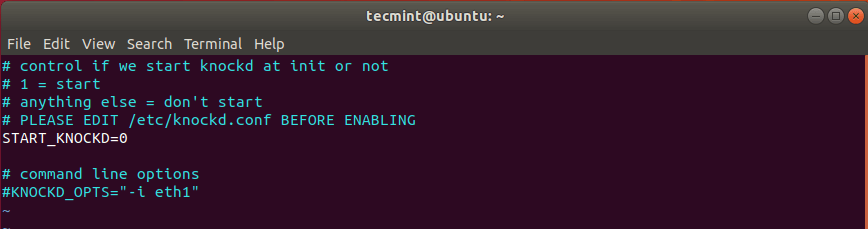
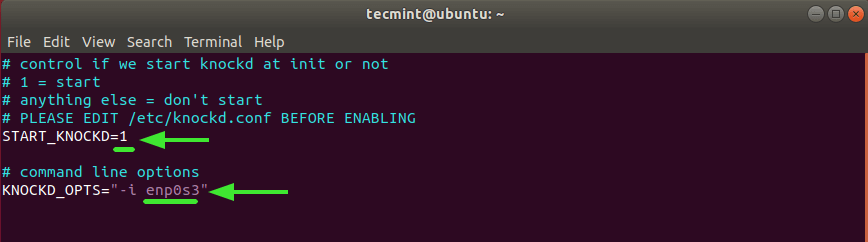
Find the line START_KNOCKD=0. Comment on it and set it to 1.
Next, go on the line KNOCKD_OPTS=”-i eth1” Comment on it and replace the default eth1 value with the active network connection of the system. To check the network interface, simply run the ip addr or ifconfig command.
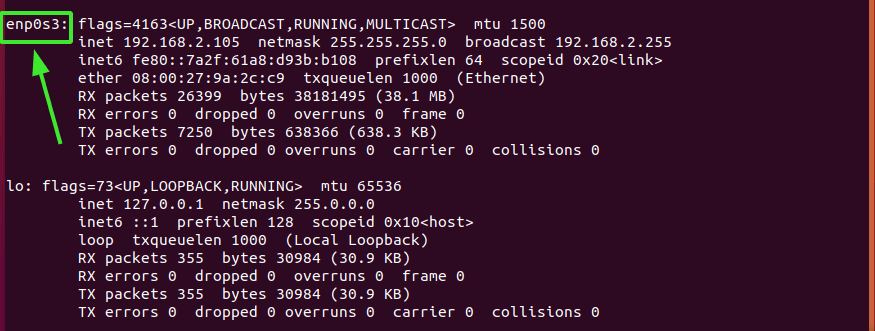
Our system, enp0s3 is the active network card.
The whole configuration is as shown.
Save changes and exit.
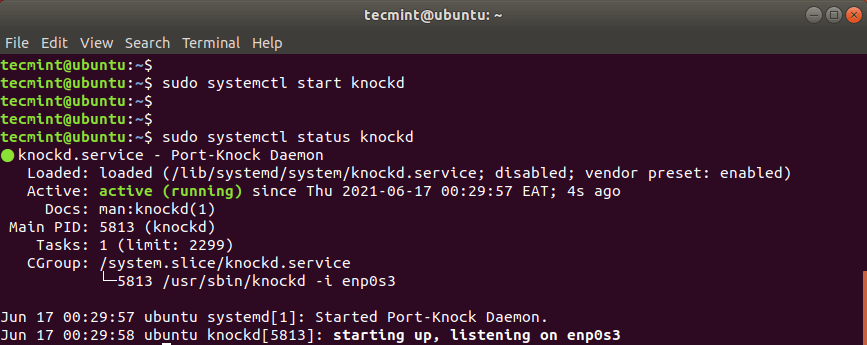
Start and then enable knockd daemon as shown.
$ sudo systemctl start knockd $ sudo systemctl enable knockd
Check knockd daemon, run the command:
$ sudo systemctl status knockd
Step 2: Close the firewall SSH port 22
Because the goal is knockd The purpose of the service is to either grant or block access to the ssh service, we close the ssh port of the firewall. But first, check the status of the UFW firewall.
$ sudo ufw status numbered
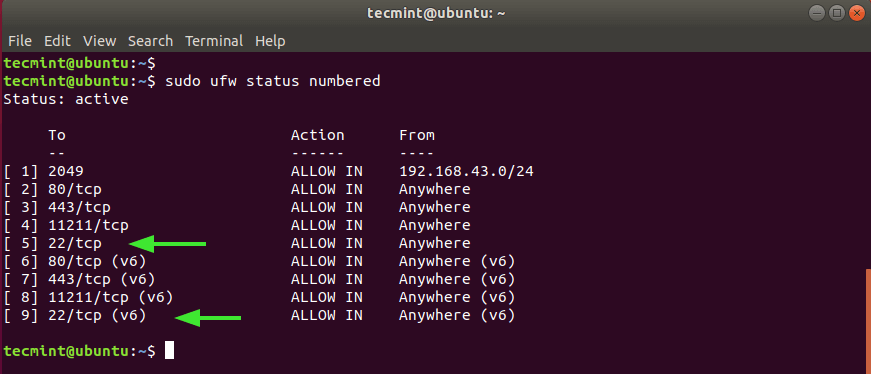
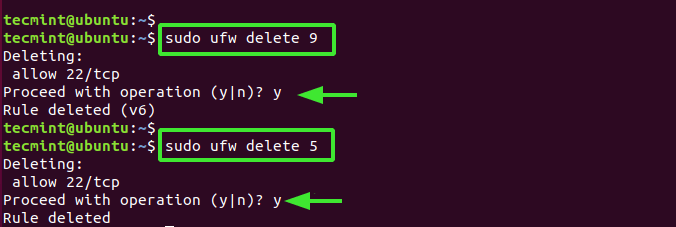
We can see it clearly from the result SSH to the port 22 is open in both IPv4 and IPv6 protocols numbered 5 and 9 respectively.
These two rules must be removed as shown in the figure, starting with the largest value 9.
$ sudo ufw delete 9 $ sudo ufw delete 5
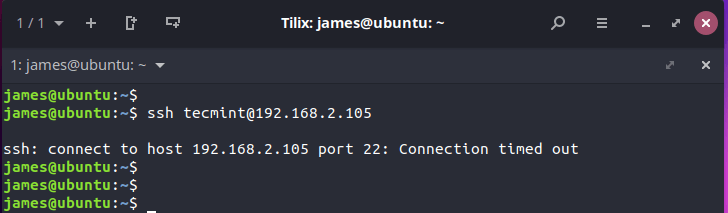
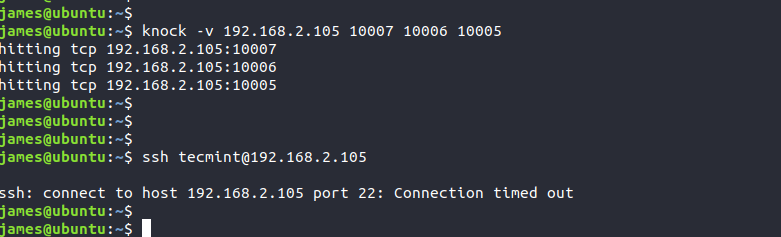
If you now try to log on to the remote server, you will receive a connection timeout error as shown in the picture.
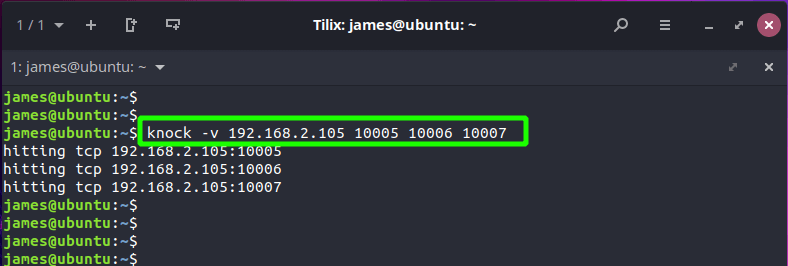
Step 3: Configure the call waiting client to connect to the SSH server
In the final step, we configure the client and try to log in by first sending the call waiting order we specified to the server.
But first install knockd daemon just like on a server.
$ sudo apt install knockd
When the installation is complete, send the call waiting sequence using the visible syntax
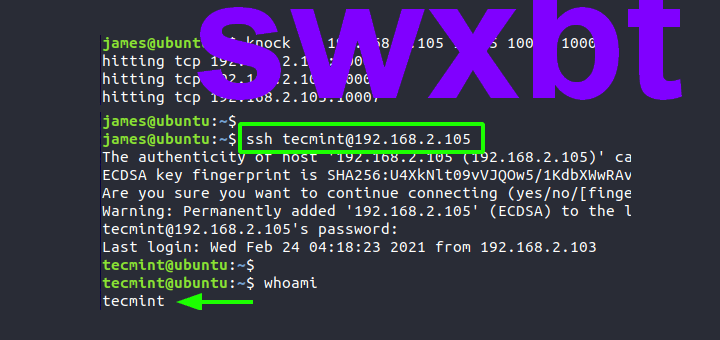
$ knock -v server_ip knock_sequence
In our case, this means:
$ knock -v 192.168.2.105 10005 10006 10007
You should get a similar output as we have, depending on your order. This shows that the call attempts were successful.
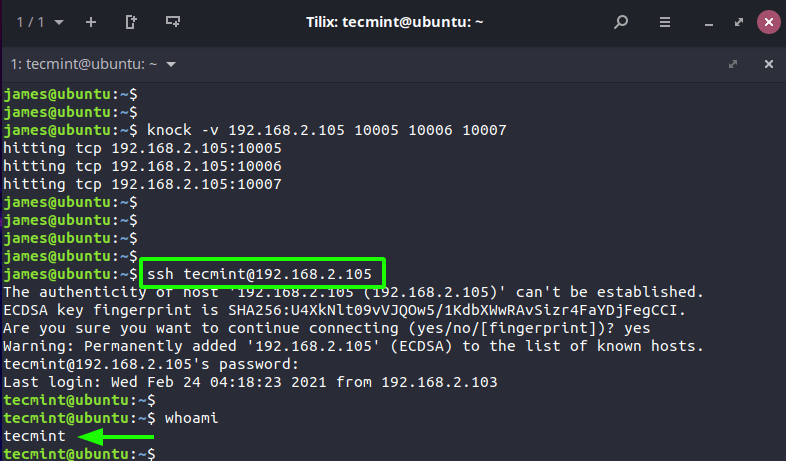
At this point, you should be able to log in to the server using SSH.
After completing the job on the remote server, close the SSH port by sending an end call waiting sequence.
$ knock -v 192.168.2.105 10007 10006 10005
All attempts to log in to the server will fail, as shown.
Decision ideas
This summarizes this guide on how port utilization can be used to secure SSH service on your server. A better and easier way would be to set up SSH authentication for your password using SSH key pairs. This ensures that only a user with a private key can authenticate on the server where the public key is stored.
Comments
Post a Comment